Smart Grid Blog 4 – January 31, 2011
Getting Smarter
Attending the Smart Grid Class reminds me of an old Russian joke that I heard from my grandfather about a Muscovite nobleman sharing a train compartment with a southern Russian from Georgia. While the lavishly dressed nobleman had a gourmet hamper of Moscow delicacies to satisfy his hunger on the long train trip, the shabbily dressed southerner produced a heap of fish heads wrapped in oily newspaper. The nobleman had often heard of Georgians’ legendary business acumen and remarkable intelligence. So he asked his travelling companion whether it was true, as folklore suggested, that this fishy repast was what made Georgians so smart? The swarthy Georgian merely shrugged. After further fruitless attempts to get a satisfactory answer, the nobleman finally proposed to swap their respective foods for the length of the journey so that he could satisfy his curiosity about this supposed correlation. Soon the Georgian was enjoying the nobleman’s sumptuous repast, while the Muscovite began daintily picking through the fish heads.
whether it was true, as folklore suggested, that this fishy repast was what made Georgians so smart? The swarthy Georgian merely shrugged. After further fruitless attempts to get a satisfactory answer, the nobleman finally proposed to swap their respective foods for the length of the journey so that he could satisfy his curiosity about this supposed correlation. Soon the Georgian was enjoying the nobleman’s sumptuous repast, while the Muscovite began daintily picking through the fish heads.
Two days later as they are approaching the final train stop in Semipalatinsk, the noble man crumpled up the last of the oily newspaper, while his taciturn travelling companion returned the now empty picnic hamper. “You know”, said the nobleman, “after eating all those fish heads I really don’t feel much smarter.”
The Georgian merely cracked a toothy grin from under his flourishing mustache and with a twinkle he allowed as how the nobleman was nonetheless “getting smarter!”
____________________________________________________________
While I am still quite unclear about where the Smart Grid begins and the dumb grid ends, and whether it is all about modernizing our infrastructure, or providing consumers with choices, or unleashing latent innovation … I think I’m “getting smarter” about Smart Grid.
____________________________________________________________________________
Utility Operations Today
– Conrad Eustis
 Conrad began by reviewing the NIST model of interoperability that we discussed at the end of the class on January 24th. He emphasized again that even though many of the functions that he had described were interoperable, they mostly used proprietary means to do so. He showed how the systems were indeed bridging the vertical silos, but often there were manual steps in the process. He pointed out that the cost of making sweeping changes were often more expensive than the benefits derived from a complete conversion, so it was reasonable to make these changes incrementally.
Conrad began by reviewing the NIST model of interoperability that we discussed at the end of the class on January 24th. He emphasized again that even though many of the functions that he had described were interoperable, they mostly used proprietary means to do so. He showed how the systems were indeed bridging the vertical silos, but often there were manual steps in the process. He pointed out that the cost of making sweeping changes were often more expensive than the benefits derived from a complete conversion, so it was reasonable to make these changes incrementally.
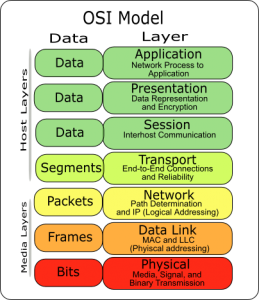
Next he introduced the OSI model – “Open System Interconnect” model. This layer architecture model was comprised of the following layers:
1. Physical Layer
2. Datalink Layer
3. Network Layer
4. Transport Layer
5. Session Layer
6. Presentation Layer
7. Application Layer
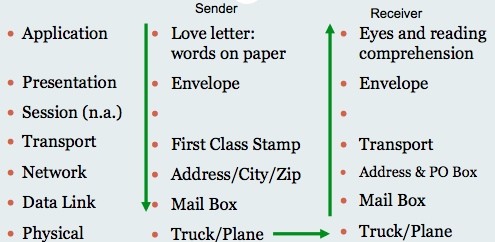
Conrad then used the example of mailing a valentine to explain the various layers:
The words in the Valentine would correspond to the “application” layer. The envelope was the equivalent of the “presentation” layer. There was no equivalent of the session since writing letters does not involve parallel activities. The transport layer was represented by the stamp that paid for its voyage. and the Network layer was about the addressing. Finally the datatlink was considered the same as the placing the letter in the mailbox, and the Physical layer was the way the way the message was actually moved – such as by truck or plane.
Importantly, it should be noted that the complete architectural layer system required that the message then reverse the flow until the message was delivered and the words were interpreted at the “application” layer, again.
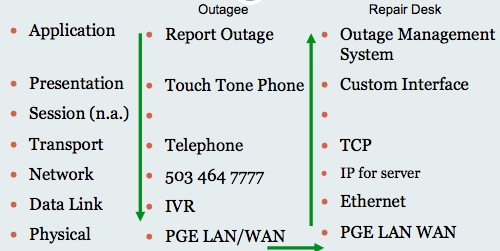
The next example showed how this OSI layered architecture analyis could be applied to the outage call system employed by the utility. In this case the report is application, the presentation is phone, Once again the session is singular. The transport layer is the telephone; the network is phone number, the data link is the IVR, etc.
Conrad went on to show how interoperability is mostly about combining two sets of data to extrapolate some useful information and implementing actions to respond to it.
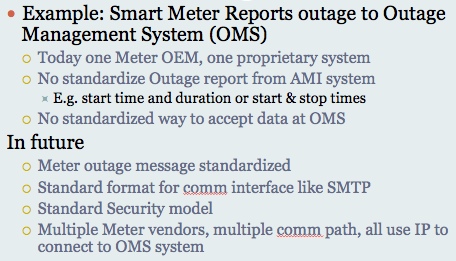 While today’s systems can report can synthesize information from the Smart meters and correlate them with customer information systems, most of these interactions are proprietary. There are no standardized ways to report the information. The bottom half of the slide explains what will be needed in the future…
While today’s systems can report can synthesize information from the Smart meters and correlate them with customer information systems, most of these interactions are proprietary. There are no standardized ways to report the information. The bottom half of the slide explains what will be needed in the future…
_____________________________________________________________
Smart Grid: Cyber-Security Concepts
– Linda Rankin
Linda’s talk fit perfectly in line with the preceding explanation of the OSI model.
Linda Rankin was an earlier graduate of the course and was later hired by PSU to co-teach the course. She was subsequently hired by QualityLogic, the firm co-founded by James Mater (part of the instructional team for this course). After these introductions had been made Conrad Eustis interjected the fact that Linda had been quite active in the development of various interfaces during her time at Intel and this work was an ideal extension of her previous work developing standard interfaces for the computer industry.
Linda began by reintroducing the OSI layered architecture stack that Conrad had referenced in the previous session, and that had been adopted as a model by the Gridwise architecture council for building a layered approach to standardized communications between the various layers of the emerging smart grid:
2. datalink
3. network
4. transport
5. session
6. presentation
7. application
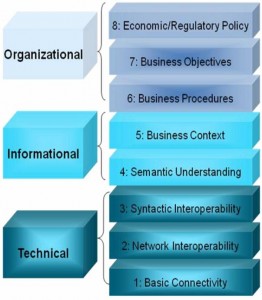
Linda discussed the various types of layers:
- Semantic layers – has to do with price
- Syntactic layers – defines the unit of measurement
- Networking layers – this is all about addresses
- Basic connectivity – wired and unwired
…and how standardizing the connections between the layers allowed development to occur more quickly. Security belongs to all layers.
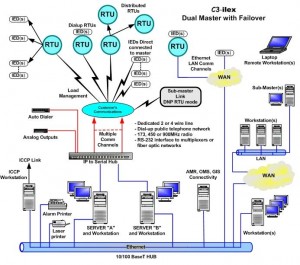
Linda then gave the class three examples of how the integration of these many layers is accomplished. To start, she explained how a SCADA system works :
A Scada system – controls many SCADA devices on an electrical network. It is comprised of:
The whole system is connected through wired or microwave communications networks. It provides two-way communications and pings the system endlessly. Scada systems were designed for reliability with stand alone functionality.
Linda then went on to explain how three typical systems work with respect to designing the linkages between the various levels of the “stack”.
1. PSU building control system
A central computer acts as server for the Siemens Building System. The system uses the 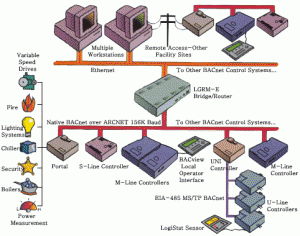 BACNET protocol to communicate between the layers. Clients can log into the BACNET. Siemens Building services runs on a schedule, supplies the algorithms. BACNET integrates all the interlayer connections via one consolidate software solution. The BACNET offers a single proprietary interface that connects with the controller, the sensor or actuator, and to non-native applications. It suffers from localized low performance and limited addressability.
BACNET protocol to communicate between the layers. Clients can log into the BACNET. Siemens Building services runs on a schedule, supplies the algorithms. BACNET integrates all the interlayer connections via one consolidate software solution. The BACNET offers a single proprietary interface that connects with the controller, the sensor or actuator, and to non-native applications. It suffers from localized low performance and limited addressability.
Part of the reason that this system is not configured to offer greater standardization is that the cost to convert old (pneumatic) system to digital costs $3000 or more. The arrangement is proprietary to reduce the need to change all the remote units tied into the interface. This system is used extensively in commercial buildings. Siemens models the building and develops the algorithms used by BACNET.
2. PGE distributed energy system: GenonSys
This system uses software known as GenonSys. In this architecture the control server is a  computer. Clients can interface into the control server, which is maintained behind a firewall at PGE. The system connects to clients (responsive assets); it communicates through Ethernet to a communication server. The communications server connects using Internet radio (high speed wireless) that has a range of 5 miles. Each site has a modem that delivers the Internet over wireless Ethernet. Each of these modems (Motorola) costs about $1000. It is totally controlled by PGE. Very similar to SCADA system, but looks like
computer. Clients can interface into the control server, which is maintained behind a firewall at PGE. The system connects to clients (responsive assets); it communicates through Ethernet to a communication server. The communications server connects using Internet radio (high speed wireless) that has a range of 5 miles. Each site has a modem that delivers the Internet over wireless Ethernet. Each of these modems (Motorola) costs about $1000. It is totally controlled by PGE. Very similar to SCADA system, but looks like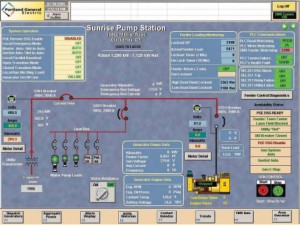
The modem communicates to the RTU’s which in turn connect to PLC’s -which then controls the responsive asset (customer’s generator). The standard is ModBus (a lot like BACNET) has a daisy chain protocol – a master slave. It queries every x seconds. It mixes the syntactic with the addressing with semantic – blends all the layers together. One ModBus can access only 247 sensors; one ModBus is deployed per home.
Home ModBus master costs about $300. Here again it may not be economical to invest in a full ISO model. The GenonSys system is really a proprietary application. It seeks specialized information necessary for managing generation. It tells us how much energy the generator putting out, how hot is the machine, fuel levels, any one in the area, etc.
Security – recent Scada exploit in UK. Once in you can get access to whole system.
3. Tendril –for home based networks.
This area has the most potential. The architecture is really an aggregator (server provider) 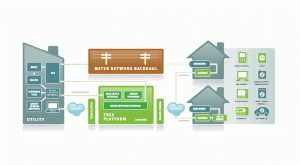 to accommodate consumer based systems. It also is supported by Open ADR. The Tendril server is based on an Open API (application programming interface).
to accommodate consumer based systems. It also is supported by Open ADR. The Tendril server is based on an Open API (application programming interface).
Tendril server – supports open API. It communicates with server via a backhaul to tendril server. Tendril server connects to internet. The internet interface could be SilverSpring, Comcast, etc – your ISP. It can go 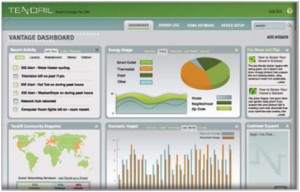 to your meter (SilverSpring) or to a gateway – your home modem. In ZigBee architecture they support a network of devices – sensors and actuators connected through wireless ZigBee interface.
to your meter (SilverSpring) or to a gateway – your home modem. In ZigBee architecture they support a network of devices – sensors and actuators connected through wireless ZigBee interface.
Home Energy Management System is a different model – is best for sorting out direct pricing.
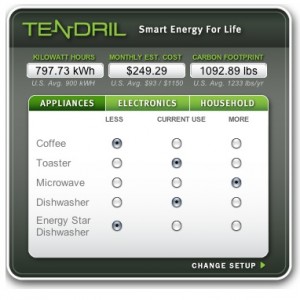 The Tendril model ultimately still needs smart appliances to be connected to this system. To be able optimize energy you you have to be conantly vigilant.
The Tendril model ultimately still needs smart appliances to be connected to this system. To be able optimize energy you you have to be conantly vigilant.
Security:
Security is an attribute across the entire stack. First you have to identify the risk. You need to keep the integrity of the system, and ensure its confidentiality. And you have to ensure the availability – especially with a scada network.
Linda finished her presentation discussing some of the following issues related to security:
- Attacks: Phishing, man-in-the middle, brute force attacks
- Authentication: Password, security, multi-factor
- Encryption: Keys, Certification (PKI), Digital signatures
- Trade-offs:
- Services offered versus security provided
- Ease of use versus security
- Cost of the security versus the risk of the loss




bookmarked!!, I love your blog!
michael kors wholesale